By Facebook
Over the past four years, industry, government and civil society have worked to build our collective response to influence operations (IO), which we define as “coordinated efforts to manipulate or corrupt public debate for a strategic goal.”
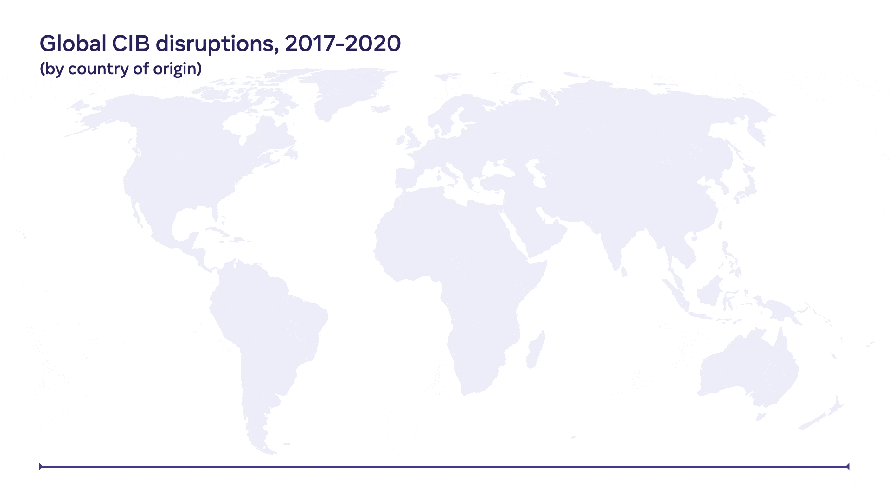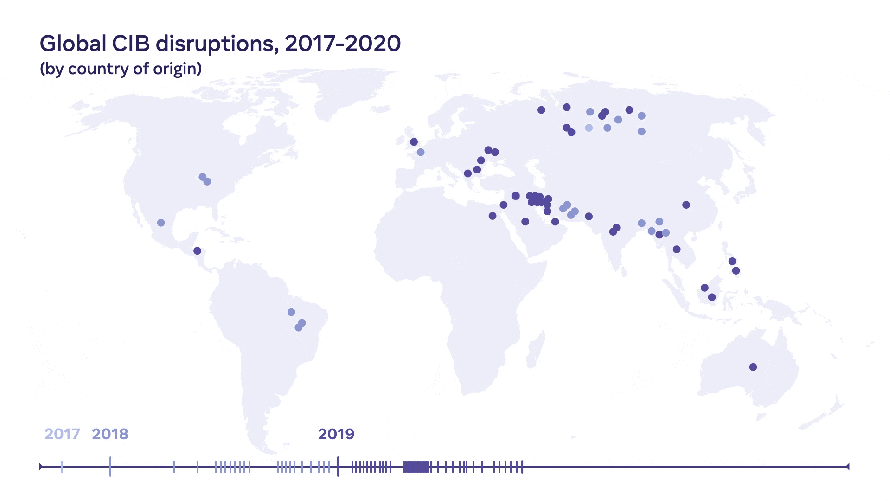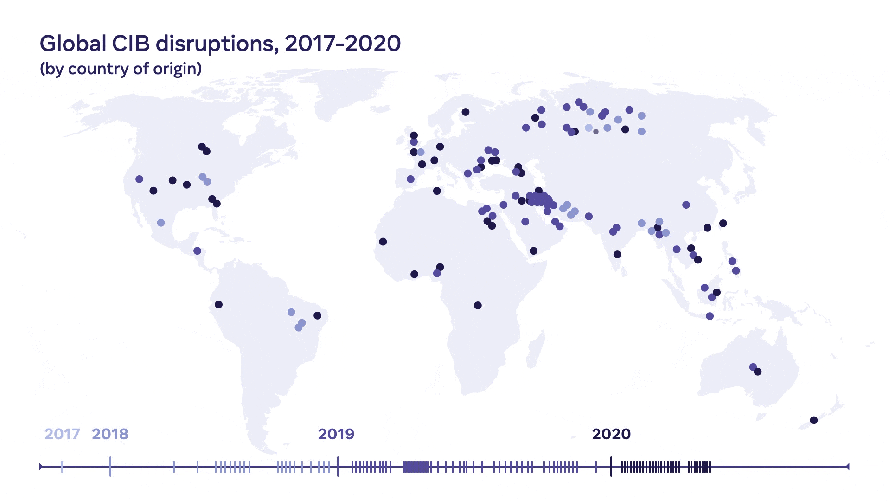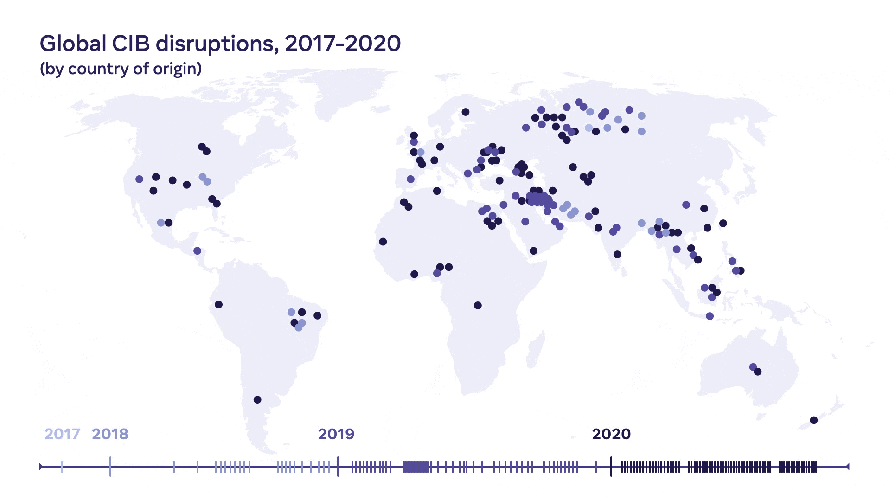
Since 2017, our security teams at Facebook have identified and removed over 150 covert influence operations for violating our policy against Coordinated Inauthentic Behavior (CIB). These operations targeted public debate across both established and emerging social media platforms, as well as local blogs and major newspapers and magazines. They were foreign and domestic, run by governments, commercial entities, politicians, and conspiracy and fringe political groups.
Today, we’re publishing a strategic Threat Report on Influence Operations that covers our CIB enforcements from 2017 through 2020. While over the years we’ve consistently shared our findings around the time of each takedown, they often are a snapshot in time focused on a particular network and its particular deceptive tactics. To keep advancing our own understanding and that of the defender community across our industry, governments and civil society, we believe it’s important to step back and take a strategic view on the threat of covert IO. In our analysis, we looked at what’s changed, how threat actors have evolved, what have defenders done that’s worked and hasn’t.
This threat report draws on our existing public disclosures and our internal threat analysis to do four things: first, it defines how CIB manifests on our platform and beyond; second, it analyzes the latest adversarial trends; third, it uses the US 2020 elections to examine how threat actors adapted in response to better detection and enforcement; and fourth, it offers mitigation strategies that we’ve seen to be effective against IO.
While the defender community has made significant progress against IO, there’s much more to do. Known threat actors will continue to adapt their techniques and the new ones will emerge. Our hope is that this report will contribute to the ongoing work by the security community to protect public debate and deter covert IO.
See the full IO Threat Report.
By Facebook




