Since spring 2014, thousands of fake LiveJournal blogs have been mass-posting content promoting a pro-Kremlin stance on world events, attacking Western leaders and praising Russian president Vladimir Putin. Using custom Python code, Lawrence Alexander was able to isolate and analyze these accounts. Delving deeper into the metadata of the supporting Twitter bot network could provide further clues as to their origin.
After my previous article exposed and examined the hundreds of Russian Twitter bots marked out by their distinctive software client names, Pat O’Reilly — a Twitter developer and creator of the Relevancy app — drew my attention to another revealing detail in the metadata. He explained that besides client names, Twitter also records the URL associated with each app authorized to use the platform. O’Reilly set up a web page (archive) with the URL records, showing that the Twitter clients controlling the bots from our dataset, including rostislav, iziaslav and pourtwi, were all associated with the same subdomain: add1.ru.
Connections to the “troll factory”
The address has an interesting history. In his June 2015 investigation into pro-Russian “troll farms” for the New York Times, journalist Adrian Chen uncovered a number of suspicious Twitter accounts posting from a tool called “mass post.” This, he found, also pointed to add1.ru, a site originally registered to St. Petersburg IT specialist and coder Mikhail Burchik. He was also listed in documents leaked by Anonymous International as the executive director of the Internet Research Agency, the alleged “troll factory” based in the same city.
Open-source information reveals connections between Burchik and the pro-Kremlin web network covered in my previous articles for RuNet Echo. WHOIS records show his name associated with the now-defunct sites worldsochi (archive) and sochiworld (archive). Nikita Podgorny, the SEO expert linked to the pro-Kremlin sites and the Internet Research Agency, is still a member of the Facebook group associated with both sites.
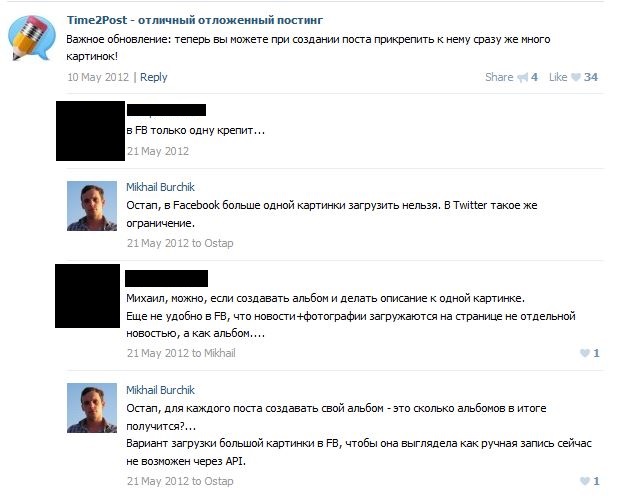
Burchik’s details also appear in the domain registration information (archive) of onlinepetitioninua.com, the URL of a website pretending to be a Ukrainian petition platform, now offline and unarchived. Its WHOIS records implausibly present the “owner” of the website to be the Ukrainian government, complete with an unlikely contact e-mail of [email protected] (username: “Ukr Gov”). Burchik’s aptitude with social media automation (Chen found he was indeed a “a young tech entrepreneur”) is reinforced by his association with the time2post app: its VK page shows him answering technical queries and posting updates to users from his personal profile:
But what else might link the add1.ru-run Twitter bots to the work of the St. Petersburg “troll farms”?
And then there was LiveJournal
A quick search of the Twitter bots’ timelines showed that a large amount of their activity has been devoted to mass-tweeting links to LiveJournal blogs. The tweets of one AlinaViatkova are a typical example:

Entering the found LiveJournal usernames into Twitter search revealed coordinated, collective activity of the part of the bots, which were repeatedly linking to the same blogs.
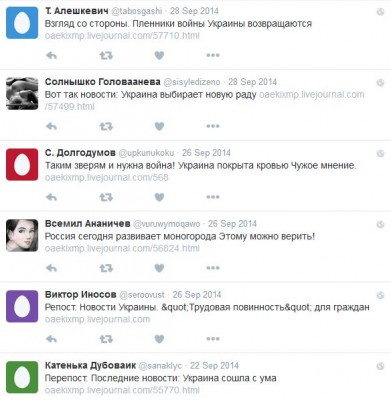
Multiple bots tweeting links to different posts by the same LiveJournal user.
The LiveJournal accounts looked immediately fake, with stock image avatars and thin or nonexistent profiles. Besides, we already know from previous leaks that the St. Petersburg “troll factory” indeed uses LiveJournal as one of its content distribution platforms. Cursory examination of this new data set suggested the posts consisted largely of pro-Russian, pro-Assad, and anti-Western sentiment.
The blogs focused, among other things, on denigrating the Ukrainian authorities (archive) and the European Union (archive) whilst portraying Putin (archive) as a noble defender of traditional Russian values. The content was typically crude (archive) in its portrayal of Ukrainian leaders.
Like the Twitter bots, the LiveJournal blogs enthusiastically promoted the Material Evidence photo exhibition (archive). Its alleged political bias and online connections with the Internet Research Agency have been previously documented by RuNet Echo.
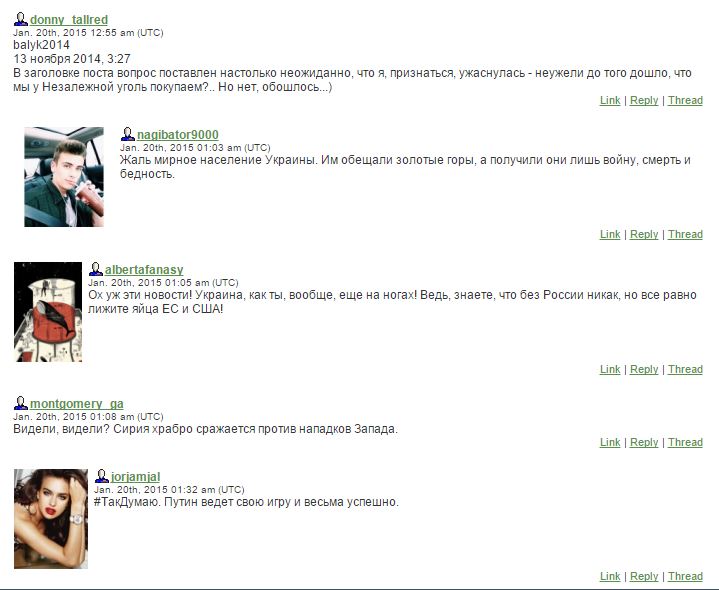
The comments beneath each post came from similar fake accounts, and tended to either reinforce the post’s political message (archive) or present a deliberately weak and simplistic “straw man” counterargument that other trolls could then knock down.
Pro-Kremlin blog network
LiveJournal has a friendship system allowing users to connect with each other, and usefully, many of the pro-Kremlin troll accounts turned out to be linked in a closed network. Using Python, I gathered the metadata of just over 8,700 connected accounts based on a few starting users by gathering their friends-of-friends. Note that, for practicality, this was not an exhaustive search, so the actual figure may be much higher.
Because of the chance of outliers in the networks (accounts unrelated to the pro-Kremlin campaign) I didn’t rely merely on friend connections, but also employed a chronological approach to isolate suspicious accounts.

Bot and troll accounts are often created en masse in a relatively short period of time. In this case, 89% of accounts in the 8,700-strong sample had been registered between early March and late May of 2014, shortly before the peak of domain registration in the previously reported pro-Kremlin website network in the summer of the same year.
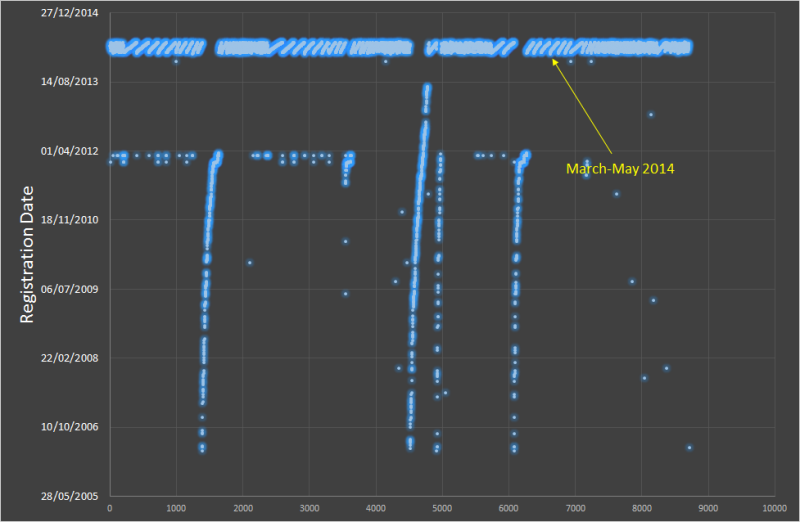
It appeared the LiveJournal accounts also had IDs that were numbered sequentially (so if Bob’s account number was 12345678 and Alice registered immediately after him, Alice’s would be 12345679.) This made it easy to modify the Python code to flag accounts created within this period. I then filtered out the irrelevant ones in an Excel spreadsheet.
Having acquired a “cleaned-up” sample, I wanted to establish the most popular posting topics across the thousands of “troll” accounts. Python came to the rescue once again: I wrote a second script to gather all the words from the titles of their recent posts. Would certain political themes characterize the entire sample?
Analysis of word frequency in post titles proved to be quite revealing. The top terms (excluding common particles of the Russian language, such as conjunctions) were “opinion,” “Russia,” “news,” “USA,” “Ukraine,” and “truth”. “EU,” “politics,” “Putin,” “Poroshenko,” and some conflict-related terms also made the list (click for a larger version of the interactive graphic).
These terms closely mirror the employee guidelines and posting topics revealed in leaked documents from the Internet Research Agency, which named Ukraine, EU, Russia, and the US among the top points of focus for the organisation.

Despite being backed by an aggressive and coordinated link-spreading strategy, it is unclear how successful these LiveJournal blogs have been in drawing in readers or influencing political opinion, either within or outside Russia.
At the time of writing, however, new posts are being produced regularly, suggesting that the 18-month-long campaign to push pro-Kremlin content on the RuNet is still underway.
By Lawrence Alexander, Global Voices





